BforeAI’s Takedown offers an enhanced “Attack lifecycle” designed to provide unprecedented transparency and efficiency. You can access a clear 30-day timeline, which accurately tracks the progress of takedowns through various stages on the "Attack Detail" page. The lifecycle includes multiple automatic contact attempts, followed by manual escalations for further review and evidence collection, if necessary.
The process is broken down into specific phases, ranging from rapid initial resolutions within hours to final efforts. While unsuccessful cases are closed after 30 days, customers can rest assured that our disruption capabilities have already mitigated the threat.
The Attack lifecycle
To access the "Attack lifecycle" timeline, you need to go into the details of an attack. You will now see a timeline similar to the one below.
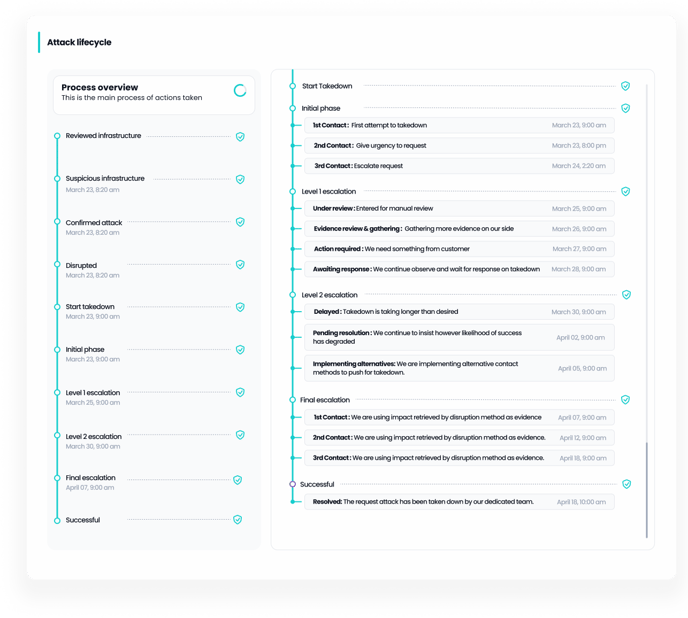
The timeline you see represents the detailed stages of our Takedown lifecycle, showcasing the progression of actions taken to resolve a malicious infrastructure attack. Here’s a breakdown of the main phases:
-
Reviewed Infrastructure: This marks the point where the suspicious infrastructure has been identified and reviewed for malicious activity.
-
Suspicious Infrastructure: This stage confirms that the identified infrastructure is indeed suspicious and potentially harmful.
-
Confirmed Attack: The attack is verified, and action plans to mitigate or disrupt the threat begin.
-
Disrupted: At this point, the attack has been sent to our disruption partner network to mitigate the malicious infrastructure.
-
Start Takedown: The process of taking down the attack starts, based on automated or manual efforts.
-
Initial Phase: This stage represents the beginning of contact with the registrar or hosting service provider.
-
Level 1 escalation: If initial efforts do not succeed, the case moves into escalation, where manual review and contact attempts occur. Here, additional actions may include:
-
Evidence Review & Gathering: Collection of more information to strengthen the takedown request.
-
Action Required: Additional input may be requested from the customer for further action.
-
Awaiting Response: We are waiting for external parties (e.g., service providers) to respond to our takedown request.
-
-
Level 2 escalation: If progress stalls, we explore alternative methods to push the takedown forward:
-
Delayed: The process is taking longer than anticipated.
-
Pending Resolution: We continue to work on the case, though the likelihood of success may be reduced.
-
Implementing Alternatives: Other strategies are employed to increase the chance of a successful takedown.
-
-
Final escalation: This is the final effort to achieve a successful takedown:
-
1st to 3rd Contact: We use evidence gathered from disruption efforts to push for final action.
-
-
Failed: If after 30 days the takedown remains unresolved, it is marked as a failed attempt, but rest assured, the disruption has already reduced the threat.
-
Successful: Once the takedown process is complete, it moves into successful, ensuring the infrastructure no longer poses a threat.
This timeline provides full transparency and ensures that every effort is made to resolve the attack, with clear updates at each stage.
