The “Attack Detail” page within the BforeAI Precrime platform provides comprehensive information and tracking features regarding identified and disrupted attacks. This interface is vital for understanding the complete lifecycle and the technical aspects of a cyber attack. This page is accessible by clicking “View details“ available on each attack.
This structured layout ensures that you can quickly understand and react to the identified attack, backed by detailed technical data and coordinated disruption efforts.

Below, I’ll explain each key section and its functionalities.
Attack Summary Panel
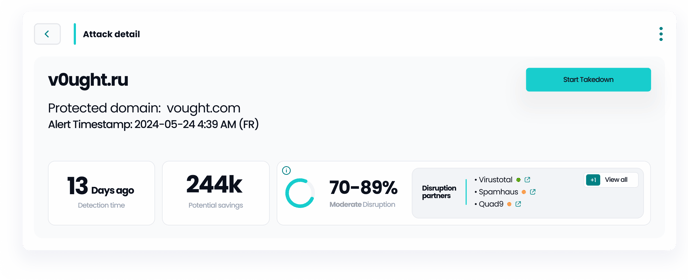
-
Protected Domain: Displays the primary domain being protected against impersonation or phishing attacks.
-
Alert Timestamp: This shows when the alert was initially generated.
-
Detection Time: Indicates how long the suspicious activity has been detected before actions were taken.
-
Potential savings: An estimation of the financial impact avoided due to early detection and disruption.
-
Disruption Effectiveness: here “Moderate Disruption“is a Percentage indicating how effectively the attack was disrupted. See this to learn more.
-
Disruption Partners: Lists the third-party services (like VirusTotal, Spamhaus, and Quad9) involved in the attack disruption process, along with their current status effectiveness displayed with colored dots. See this to learn more.
AI Feedback

-
The image on the right is a static screenshot captured during the detection phase. It is not currently being updated.
-
Provides automated insights from BforeAI’s systems about the specific characteristics of the attack, such as domain registration details, DNS configurations, and redirects.
-
It may also include specific findings from our analyst team as comments.
Attack Lifecycle
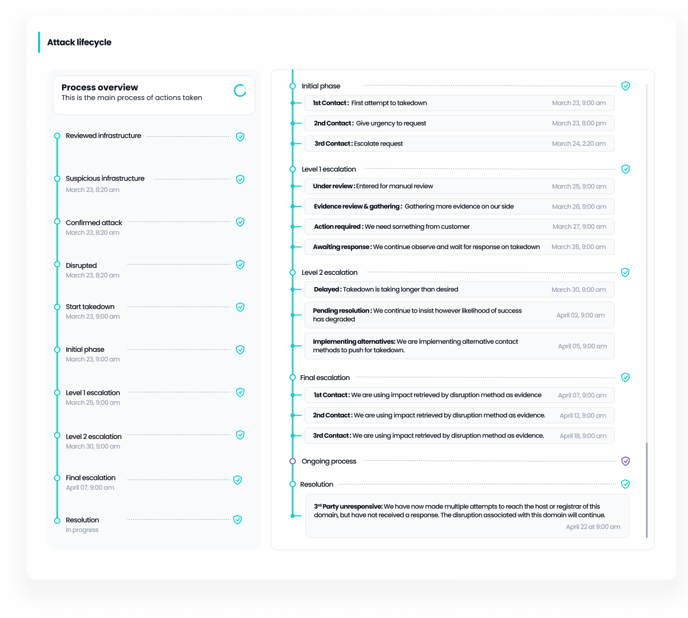
-
Outlines every phase of the attack from initial detection to ongoing processes or resolution. Each step, such as “Reviewed Infrastructure,” “Confirmed Attack,” and “Disrupted,” is marked with a timestamp and the current status.
-
Learn more here
Technical Details of the Attack
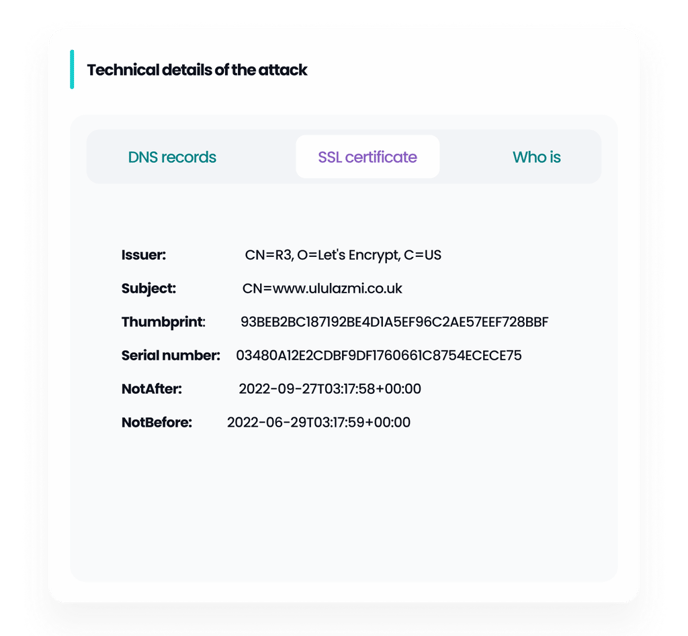
This card contains specific information about the attack domain. This information was gathered during the detection phase and is not currently being updated.
-
DNS Records: Shows the Domain Name System records associated with the malicious domain. Based on what we manage to gather, we typically come across:
|
Address: |
Domain Name: |
Initial Time To Live |
Record Class |
Record Type |
Time To Live |
Server |
|---|
-
SSL Certificate: Displays details of the SSL certificate found at the domain. We provide the following information:
|
Subject: |
|
Thumbprint: |
|
Serial Number: |
|
NotAfter: |
|
NotBefore: |
-
Whois Information: Contains the registration details of the domain, often used to identify the registrant behind potentially malicious domains. It contains all the Whois in TXT format.
Domain Connections

-
Visual network graph displaying the relationships between the primary malicious domain and other related domains, categorized by their threat level (e.g., “Bad,” “Good,” “Neutral”) and roles in the attack infrastructure.
-
"Sno" refers to the connection domain number;
-
"Domain" represents the name of the connected domain;
-
"Role" describes the nature of the relationship between the attack domain and its connection. Often, if marked as "requested," it indicates that the attacking domain is seeking data from its connection;
-
"Score" reflects the Precrime intelligence rating.
-
